In Windows Operating System There is a File which Called NTUSER.DAT File Everyone has Question Regarding it What is Actually? When we create the user in Windows The NTUSER.DAT file Created Automatically. It contains personal files and preference settings that are specific to each user. Each profile of User Contains Different Like Document, Personal Files, History, and Much More things.
Contents
What is the NTUSER.DAT File?

Portable applications usually keep their configuration data within files in the directory or folder from where the application executable runs. The registry also keeps track of users activities, stores their settings, and supports the multi-profile structure, where each user has their configuration for their account. The registry of each user stores under that user’s directory in a separate file called NTUSER.DAT.
NTUSER.DAT file keeps a record of all the user related things in the Database of Windows and It’s called Windows Registry which Keeps the information Regarding Registry of Windows.
Location:
It will be located in User Folder in Operating System. In Windows 10, Windows 8/8.1, Windows 7 The NTUSER.DAT File is Located at
C:\USERS\Your_Username
How to View NTUSER.DAT File?
The NTUSER.DAT file Confidential in Windows OS because It contains user information of the particular user. so, If you want to delete NTUSER.DAT file then It also not possible to delete this file. you can unhide windows hidden file by going From windows Folder Options Menu and select “Show Hidden Files, Folders and Drives” in the Advanced Settings pane and then click “OK.”
This file is used for Do forensics for various cybercrime. we can gather evidence, artifacts and much more user containing information. It gives every information regarding the user in windows operating system.
Delete NTUSER.DAT FILE
NTUSER.DAT is private system file for that user. If you have the privilege to delete that user, then you can delete. Otherwise, take ownership and do it. more Info to take ownership. It is normally locked you can’t delete this file. The only system administrator can delete child user NTUSER.DAT File. But you can’t delete administrator-level account’s NTUSER.DAT File. so, at final you can’t delete this file if you have not privileged to it.
How to Do NTUSER.DAT forensics?
using this file we can get some artifacts from windows system NTUSER.DAT File gives us much information like user Assist, MRU ( Most Recent Used) List, Volume Serial Numbers, Typed URL’s, Recent Docs, Current Control Set and Much More Details regarding windows.
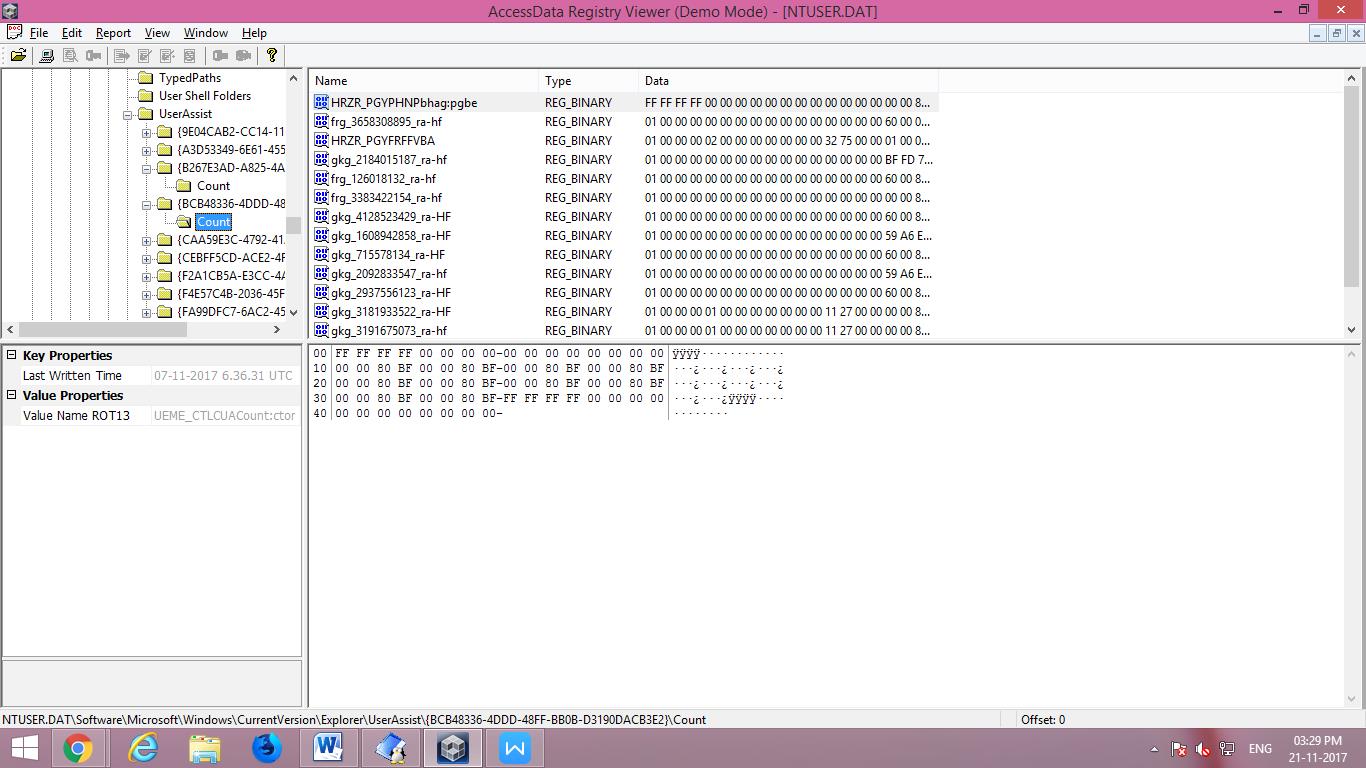
How to Get User Assist Using Registry Editor?
Step 1: Open NTUSER.DAT File in Access Data Registry Viewer
Step 2: Go To This Path:
NTUSER.DAT > Software > Microsoft > Windows > Explorer > User Assist
Step 3: You can Check There some and Check Their Value Properties.
Value Name Rot 13 Found Means This Algorithm is Applied.
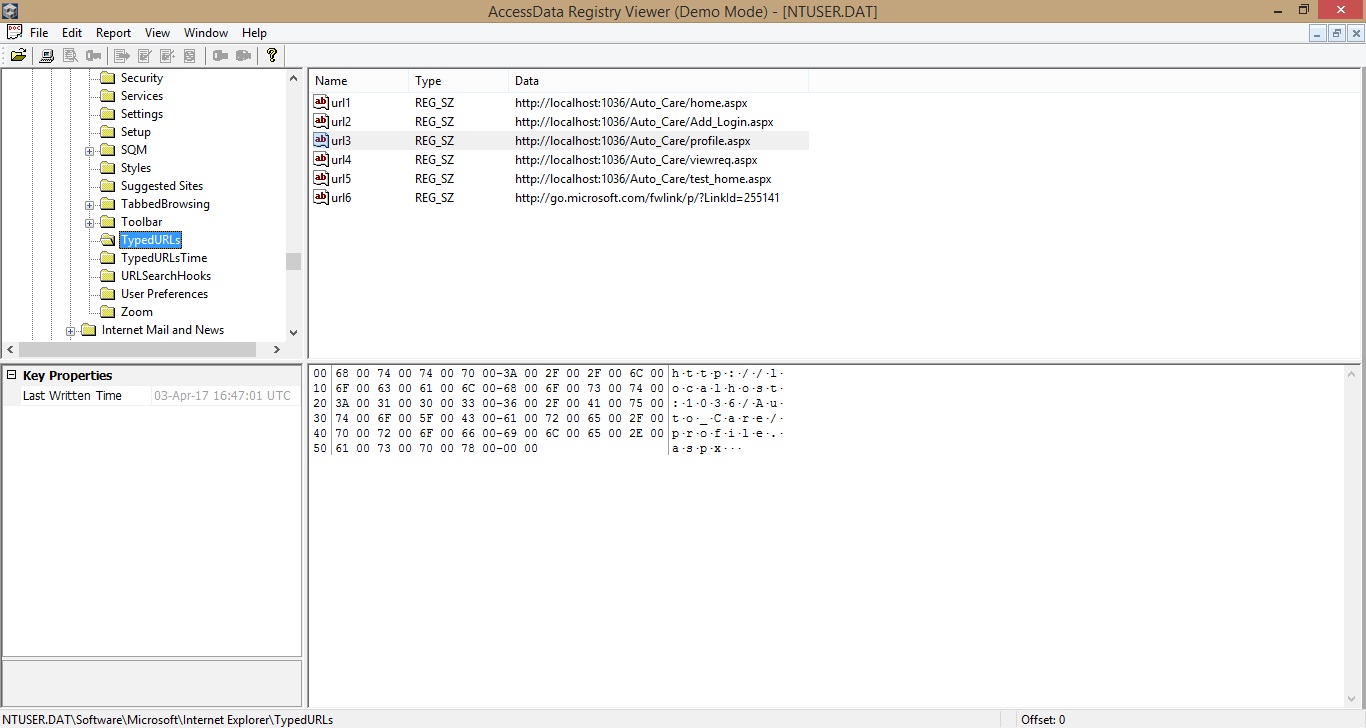
How to View TypedURLs with Registry Viewer or TypedURLs registry key?
What is TypedURL?
TypedURLs data is a strong indicator of Web pages the user deliberately visited, although there are some complications in its interpretation.
Procedure:
Step1: Open the Registry Viewer and
navigate to,
RegistryImage\Users\Student\NTUSER.DAT
Step2: Registry Viewer is similar to REGEDIT. Now navigate to,
NTUSER.DAT\Software\Microsoft\Internet Explorer\TypedURLs
Result:
The right pane should now show the URLs that have been visited, as shown below:
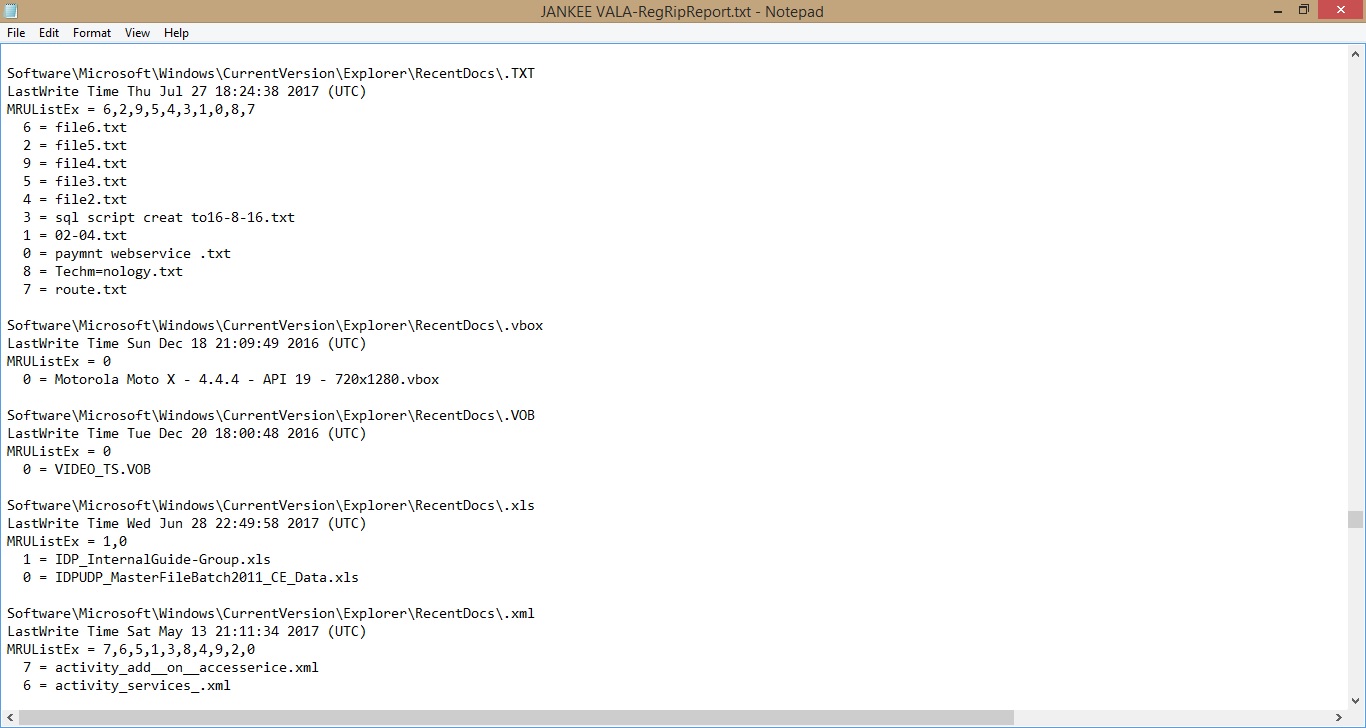
How to View RecentDocs with RegRipper?
RecentDocs shows documents the user opened recently. Download RegRipper First.
Procedure:
Step1: Open the RegRipper and it shows the hive files. Now navigate it to,
RegistryImage\Users\Student\NTUSER.DAT
Step2: In RegRipper,
in the “Report File:” line clicks the Browse button and make RegRipReport file and in the “Profile” line, select ntuser-all. Now Rip it.
Step3: Open the RegRipReport file and find RecentDocs\ where you can see some recently opened files and the “LastWrite Time”
Result:
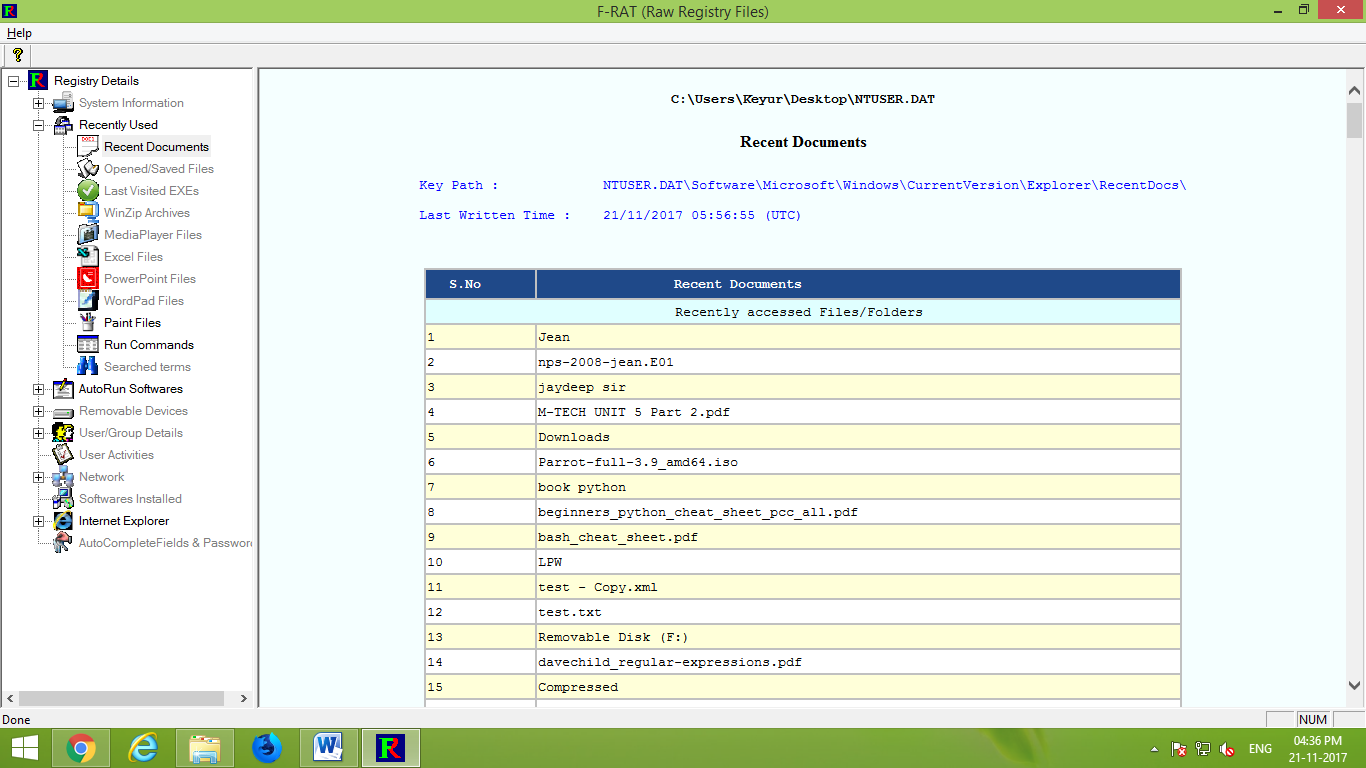
How to Do NTUSER.DAT forensics with Automated Tools?
Using F-RAT Software By C-Dac 3rd Party Tool
Step 1: Download F-Rat Software and Open F-Rat
Step 2: Open Registry File in That and Check Every Evidence which we need
Like Recent Files, Autorun Software, User/Group and Every Detail.
Step 3: Import Other Files Like SAM, Default, Security, Software, and System
Here is The Example Of NTUSER.DAT File
Analysis OF SAM File:

Conclusion:
At the final step, we get registry from manual and automatic techniques. We find different artifacts from the registry.
