Ports are channels through which information can be transferred. Contrary to the common perception of hardware ports such as USB ports, the article is in fact about software port 135. But they do share some sort of similarity in their function.
The article is about one port, in particular, port 135. You probably have a lot of questions about this port in your mind since there is not much organized info about the port on the internet. So in this article, we will go over the basic meanings of software ports, port 135, and a bunch of related terms. We will also show you why and how you can close the port.
Contents
What exactly is a port?
There is no way that you are not familiar with the term ‘ports’ when it comes to hardware. Indeed you must have used a USB port at some point in your life. A port is an interface between your computer and external devices such as printers, mobiles, portable storage devices, or other computers. They make use of data cables or chords to establish a link through which the flow of information takes place. But the topic at hand is not about these ports.
The ports that we mean have a software origin. Nonetheless, they serve the same purpose. These ports are locations to which data can be sent. They also do the job of recognizing this data and then handling them as required. But to put it more technically, ports are logical constructs in an operating system to identify a specific process or network. The port in the discussion, i.e. port 135, is one of the many used in Windows OS.
TCP and UDP
Regardless of what kind of port you are going to read about, you will surely come across these two words a lot. So, it is obvious that you need to get a good grasp of what they actually mean. These terms are associated with the dispatch of bits of data otherwise called packets.

First, they travel from your computer to your router. Thereafter, these packets make their way to a particular IP address. The first one, TCP, stands for Transmission Control Protocol. It is the protocol that makes it possible for you to mess around with the internet as you do.
When you search for something using a browser, you are actually trying to get into a new webpage. So, TCP sends a particular set of packets to the server’s address. Consequently, the server transmits a response likewise. The data received is then rearranged, like solving a puzzle, and you finally get to the web page.
The word, UDP, stands for User Datagram Protocol. It uses datagram for the dispatch of data and it is rather similar to packets. The key difference between UDP and TCP is that UDP will keep on sending one set of data after the other without caring about receiving responses.
On the other hand, TCP will resend a packet if it does not receive a response. Hence TCP is more responsible. Furthermore, checks the data it transmits for errors or corruption. But by eliminating the checking and receiving response processes, UDP is certainly a lot faster than the two.
What is Port 135?

It is the port that is mainly used in client-server relations, one among several ports that are used in the Windows Operating System. Client-server relation is one where a party called the client, you in the majority of the time, requests for a particular information or access to a particular area, and the server provides it. It is also closely involved with RPC and DCOM.
RPC stands for Remote Procedure Call. When you perform an action on your computer, your CPU runs the required procedures for it. Whereas in remote procedure calls when you perform an action, its procedure can be run by some other computer or device in the network.
DCOM stands for Distributed Component Object Model and it consists of several programs and concepts that help the client program to send requests to the server in a Windows Operating System environment. Port 135 is one of the main interfaces that help out DCOM.
Port 135 exploit
While being very useful and essential to the working of your computer, ports, in general, are gateways to your system. Hence an open port may just be what an outside may be looking for in order to extract your private information or to infect your system.
All the services and applications in your PC can, therefore, become an easy target. You certainly can’t risk opening Port 135 to the internet unnecessarily. There are hacking tools out there that can easily recognize the DCOM-related activities in your system and easily exploit vulnerabilities.
How to check live status of port 135?
Before going through the whole procedure of closing a port you might want to first check if the port is actually open or not. You can use the Command prompt to achieve this without much hassle. In fact, the following procedure will give you the details of several ports or not. It is the fastest way to find out if ports are listening or not.
- Use your keyboard to press the Windows key and R key simultaneously.
- The Run dialogue box will appear. In the space against open, type in cmd and then press Enter or choose OK. Alternatively, you can use the Windows Search bar to look for cmd or Command prompt.
- Once the command prompt opens, type the following command and press Enter: netstat -na
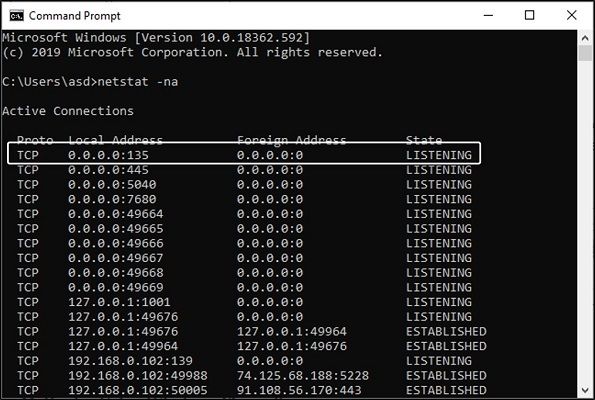
The process of scanning all the ports of your port occurs next and it completes in the blink of an eye. You will be quickly shown the results on the screen. Find TCP port 135 under the local address column and if its state says “LISTENING” then it will be open.
How to close port 135 Windows?
At first, there is no absolute need for disabling port 135 for normal PC users. But if you are working around pirated, cracked versions of software regularly, you may want to disable TCP port 135 to avoid intrusion of harmful ransomware like WannaCry.
Method 1: Using Windows Firewall
This is the easiest method out there to close this port. It may seem a little wordy and long but don’t worry. Because most steps just include clicking options kind of how you install a game on your computer.
- Place the cursor on the Windows Search bar.
- Now, type in Control Panel and then press the Enter button.
- You will quickly get the search results. Open the app from them.
- Here you can see several tiles. Proceed to choose the System and Security option.
- Next, select Windows Defender Firewall.
- On the left pane, you will see an option called Advanced Settings with a small shield icon. Choose it.
- Look at the left side yet again, there will be a lot of tiles. From them, choose the Inbound Rules option.
- This time around, look at the right side. And then select the New Rule option once you find it.
- A new window will open. Here you have to select the Port option and then hit Next.
- You will be faced with two questions. For the first one, you would want to choose TCP.
- For the second one choose Specific local ports and type in 135 in the accompanying space. Hit Next once you are done.
- On the next page go right ahead and choose the Block the connection option and then proceed with Next.
- Be sure to tick in the three checkboxes provided and then go on to the next page.
- Give it a name and description as you wish and then bring it home by hitting Finish.
- If you want to check the rules that you just set up open its properties.
- Click on the Protocols and Ports tab.
- Now you can check under Local Port.
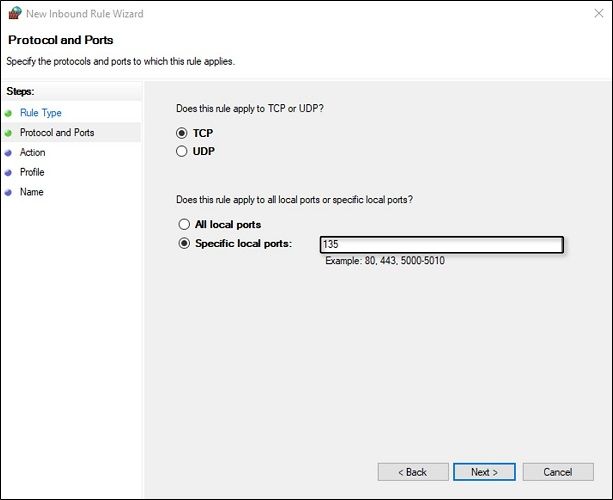
In some cases, the Port will only close after a reboot.
Method 2: Using Registry Editor
The Registry Editor is a pretty neat tool that you can use to modify a lot of programs on your PC. But do keep in mind that it is a database for all the system files and installed applications on your computer. Therefore be very careful while operating it.
- Open the Run dialogue box by pressing the Windows key and R key on your keyboard simultaneously.
- In the space beside open, type in Regedit and then press OK or hit Enter. (You can always use the windows search bar instead. Just type in Registry editor or Regedit and hit enter. Then you can find it in the search results.)
- On the navigation pane on your left side, expand the HKEY_LOCAL_MACHINE by using a double-click.
- Now look for the SOFTWARE file under it and expand it as well.
- Similarly, expand the Microsoft file and then proceed to open the Ole key under Microsoft.
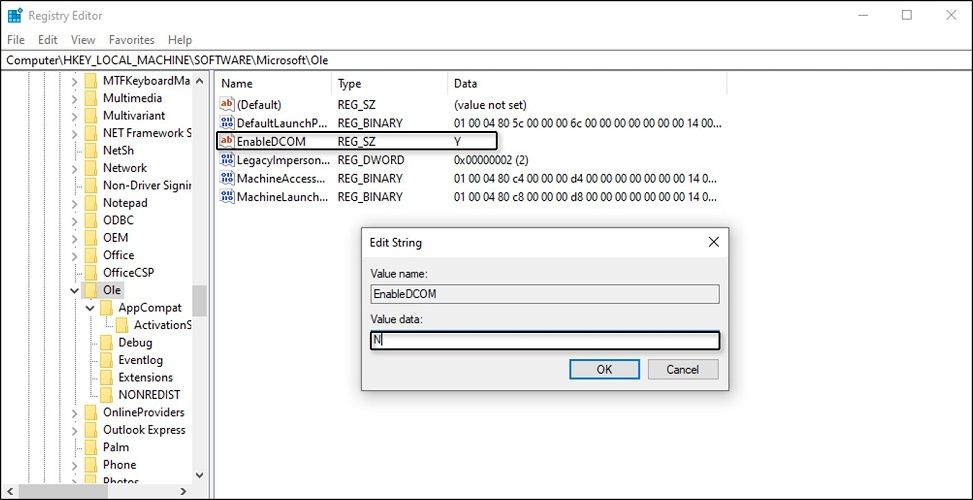
- Look to the right side of the screen. Double-click on the EnableDCOM option.
- Once it opens, change its data value from Y to N.
- Once this is done, navigate to this registry key: HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ RPC
- On the right side, double-click on the DCOM Protocols option. You will see some data under the value data tab. Select it all and then delete it. This will leave it blank and that’s the way you need it to be.
- Port 135 has now been closed.
To disable other programs or services related to DCM, follow Control Panel >> Administrative Tools >> Services. Then disable these services: COM+ Event System, COM + System Application and, System Event Notification.
Wrapping up,
You have now learned a decent bit about port 135. We have also discussed checking port listening and closing the port. Do try out some tinkering with it if you need to. But be careful though and you should know what you are doing.
